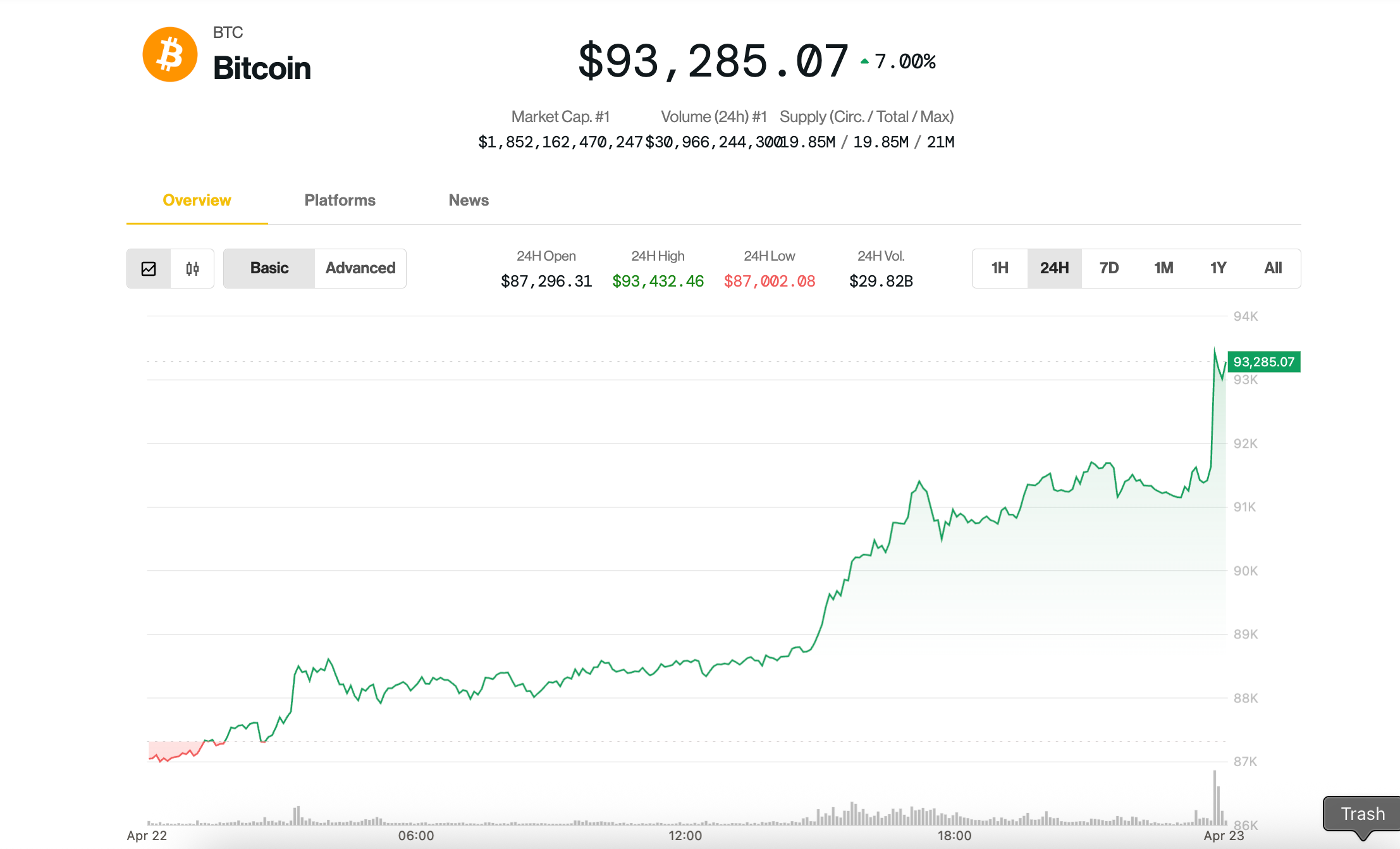
Bitcoin and Ethereum Stuck in Range, DOGE and XRP Gain
April 25, 2025
1. Introduction
When a hacker compromises a cryptocurrency, it means that unauthorized access has been gained to a system, potentially leading to theft or manipulation of digital assets.
2. Importance
The compromise of a cryptocurrency can have significant implications for investors, traders, and the overall market. It can result in financial losses, reputational damage, and undermine trust in the security of digital assets.
3. Technical Background
In the cryptocurrency industry, security is paramount to protect against hackers and cyber attacks. However, despite advancements in technology, hackers continue to find vulnerabilities in systems to compromise cryptocurrencies and steal funds.
4. Usage
When analyzing a cryptocurrency, it is important to consider the security measures in place to prevent hacking incidents. Traders should also be vigilant in monitoring their accounts and taking precautions to safeguard their assets from potential compromises.
5. Risk Warning
The compromise of a cryptocurrency poses a significant risk to investors and traders, as it can result in substantial financial losses. It is essential to use secure wallets, employ strong passwords, and implement two-factor authentication to mitigate the risk of hacking.
6. Conclusion
In conclusion, understanding the implications of a hacker compromising a cryptocurrency is crucial for anyone involved in the industry. By staying informed and taking proactive measures to enhance security, individuals can help protect their digital assets from potential threats. Further research and education on cybersecurity best practices are recommended to safeguard against hacking incidents.
1. Can a hacker compromise my personal information?
Yes, a hacker can potentially access sensitive data such as passwords, credit card information, and personal documents if they successfully compromise your system.
2. How can I tell if a hacker has compromised my device?
Signs of a compromised device include unusual activity, unauthorized logins, and unexplained changes to settings or files.
3. What should I do if I suspect a hacker has compromised my accounts?
Immediately change your passwords, enable two-factor authentication, and contact the affected service providers to report the breach.
4. Is it possible to recover from a hacker compromising my system?
Yes, by taking swift action to secure your accounts, remove malware, and update software, you can mitigate the damage caused by a hacker.
5. How can I protect myself from future hacker compromises?
Regularly update your software, use strong, unique passwords, be cautious of phishing attempts, and consider using security measures like antivirus software and firewalls.
User Comments
1. “I can’t believe a hacker compromised my account! This is a nightmare!”
2. “My bank account was hacked and now I’m freaking out. What do I do?!”
3. “Ugh, why do hackers have to ruin everything? So frustrating.”
4. “Feeling violated after finding out a hacker compromised my personal information.”
5. “I thought I was being careful online, but a hacker still managed to breach my security. It’s scary.”
A hacker compromised a ZKsync admin account on April 15, minting $5 million worth of unclaimed airdrop tokens, according to ...
Read more© 2025 Btc04.com